What safety certificates shouldn’t be on my Android? This important query delves into the intricate world of cellular safety, highlighting the significance of understanding which digital signatures pose a risk to your machine’s integrity. We’ll navigate the panorama of certificates, revealing the potential risks lurking inside seemingly innocuous digital credentials, empowering you to safeguard your Android from malicious intrusions.
Studying to identify and take away undesirable certificates is a crucial step in making certain your machine stays a safe and dependable platform.
Android gadgets, like all subtle system, depend on safety certificates to confirm the authenticity of functions and web sites. Nonetheless, not all certificates are created equal. Some may be malicious, posing a big threat to your information and privateness. This information will show you how to determine probably dangerous certificates, perceive the dangers they pose, and learn to take away them safely.
We’ll additionally discover preventative measures to maintain your Android protected against future threats.
Introduction to Android Safety Certificates

Android, the ever-present cellular working system, depends closely on digital certificates to make sure the safety and integrity of apps and system parts. These certificates act as digital signatures, verifying the authenticity and trustworthiness of software program and information. Understanding these certificates is essential for anybody utilizing Android gadgets to guard themselves from malicious actors.Safety certificates in Android are primarily digital paperwork that bind an id (e.g., an app developer) to a public key.
This public secret is used to encrypt communication and confirm the authenticity of the sender. Consider it like a digital passport, verifying who’s who within the digital world. Various kinds of certificates serve completely different functions, making certain a layered strategy to safety.
Forms of Android Safety Certificates
Varied certificates play essential roles in Android’s safety structure. They authenticate app builders, make sure the integrity of downloaded apps, and safe communication channels.
| Certificates Sort | Description | Typical Utilization | Potential Dangers |
|---|---|---|---|
| Software Signing Certificates | Used to digitally signal Android functions. These certificates confirm the developer’s id and make sure the software hasn’t been tampered with since its launch. | Authenticating app builders and verifying app integrity. | Compromised certificates can permit malicious actors to impersonate builders or inject malicious code into functions. |
| System Certificates | Important for verifying the authenticity of system parts and providers. These certificates are embedded within the Android OS itself. | Securing system communications and stopping unauthorized entry to crucial system features. | Compromised system certificates may permit malicious actors to achieve management over all the machine. |
| Trusted Root Certificates | Type the muse of the certificates chain, making certain the authenticity of intermediate and end-entity certificates. | Establishing belief within the certificates chain. | Compromised root certificates would undermine all the belief system, resulting in potential safety breaches in all functions and providers. |
| SSL/TLS Certificates | Used to encrypt communication between functions and servers, making certain confidentiality and information integrity. | Securing delicate information switch between apps and web sites, particularly when dealing with logins or monetary transactions. | Malicious actors may intercept or manipulate communication if the SSL/TLS certificates is compromised. |
Figuring out Undesirable Certificates
Your Android machine, a digital fortress, can typically accumulate certificates which can be extra like unwelcome company than trusted allies. Realizing how one can spot these intruders is essential for sustaining a safe surroundings. These certificates, although seemingly innocuous, may probably unlock pathways for malicious actions. This part particulars the traits and purple flags to be careful for.Undesirable certificates can originate from numerous sources, typically masking themselves as respectable entities.
They may be remnants of earlier installations, compromised apps, and even fraudulent makes an attempt to achieve entry. Studying to determine these certificates empowers you to proactively safeguard your machine.
Recognizing Suspicious Certificates
Certificates, of their essence, are digital signatures, making certain the authenticity of an internet site or software. Nonetheless, some certificates exhibit traits that recommend a possible risk. These traits act as indicators of doable compromise or pointless presence.
Standards for Figuring out Potential Threats
A meticulous examination of certificates particulars can reveal potential safety dangers. Search for uncommon or inconsistent info. The issuer’s repute, the certificates’s validity interval, and its objective all present insights. Mismatches or inconsistencies in these parts elevate purple flags.
Traits of Dangerous Certificates
Sure traits typically accompany certificates related to safety dangers. One notable attribute is an unusually quick validity interval. Certificates with excessively quick durations may sign a short lived or fraudulent id. Moreover, certificates issued by unknown or untrusted entities warrant fast scrutiny. An unfamiliar issuer is a robust signal of potential manipulation.
Certificates Format Differentiation
Certificates are available in numerous codecs, every with distinct traits. Understanding these codecs is important for figuring out discrepancies. The commonest format is the X.509 format. X.509 certificates sometimes comprise details about the certificates’s topic, issuer, validity interval, and public key. Distinguishing between these codecs helps in recognizing anomalies.
A poorly formatted certificates or one with lacking fields may point out manipulation.
Indicators of Dangerous Certificates
Figuring out probably dangerous certificates entails recognizing key indicators. A certificates with an invalid signature is a transparent warning. Likewise, a certificates with a mismatched or uncommon area title or IP handle ought to elevate concern. One other potential indicator is a certificates issued for a website or IP handle that doesn’t correspond to the supposed recipient. Lastly, certificates used for non-standard functions (similar to unauthorized entry or information transmission) needs to be flagged.
- Invalid Signature: A crucial indicator of potential tampering or forgery.
- Mismatched Area/IP: A certificates supposed for one area however used for an additional is a trigger for concern.
- Unfamiliar Issuer: Certificates from unknown or untrusted entities needs to be handled with warning.
- Excessively Brief Validity: Certificates with unusually quick validity durations may sign a short lived or fraudulent id.
- Uncommon or Non-Customary Objective: Certificates used for unauthorized or non-standard functions needs to be examined completely.
Potential Dangers of Undesirable Certificates
Undesirable safety certificates in your Android machine are like hidden traps in a digital minefield. They will compromise your privateness and safety, making your telephone weak to malicious actors. Understanding these dangers is essential for safeguarding your information and sustaining a safe digital life.Malicious certificates, masquerading as respectable ones, can open doorways for attackers to entry delicate info, and even take management of your machine.
These aren’t simply theoretical threats; they’ve real-world penalties, and recognizing them is step one in direction of prevention.
Safety Vulnerabilities
Undesirable certificates create vital safety vulnerabilities by permitting attackers to bypass regular safety protocols. This primarily tips your machine into trusting fraudulent connections. This may occur by means of numerous strategies, and the implications will be extreme.
Exploitation Strategies
Attackers can leverage undesirable certificates in a number of methods. They could craft faux web sites that mimic respectable ones, utilizing the certificates to ascertain a seemingly safe connection. This permits them to intercept your information as you navigate these websites, together with usernames, passwords, and monetary info. One other approach entails injecting malicious code into apps which have been granted entry to delicate information.
The certificates, put in surreptitiously, can open the door for such a assault.
Assault Examples
Think about a faux banking web site that appears similar to the true one. An attacker may set up a certificates that makes your machine belief this faux website. Once you enter your banking particulars, they’re intercepted and stolen. Or, take into account a seemingly innocent app that you just obtain. The app may have a malicious certificates put in that enables it to entry and steal your private info, like contacts or images.
Penalties of Malicious Certificates
The results of getting malicious certificates put in can vary from minor inconveniences to extreme monetary and private harm. Think about your on-line banking account being emptied or your personal images being leaked. The affect will be devastating, each financially and emotionally. The theft of delicate info can result in id theft, fraudulent fees, and the lack of your hard-earned information.
Comparative Evaluation of Assault Sorts
| Assault Sort | Description | Potential Influence |
|---|---|---|
| Man-in-the-Center (MITM) Assault | Attacker intercepts communication between the consumer and a respectable service, utilizing a fraudulent certificates to achieve belief. | Information theft (passwords, monetary info), unauthorized entry to accounts, potential machine compromise. |
| Certificates Spoofing | Making a faux certificates that mimics a respectable one, tricking the machine into trusting a malicious website. | Information breaches, monetary fraud, phishing scams, id theft. |
| Malware Injection | Utilizing the certificates to put in malicious software program that good points unauthorized entry to delicate information. | Information theft, distant management of the machine, unauthorized entry to accounts. |
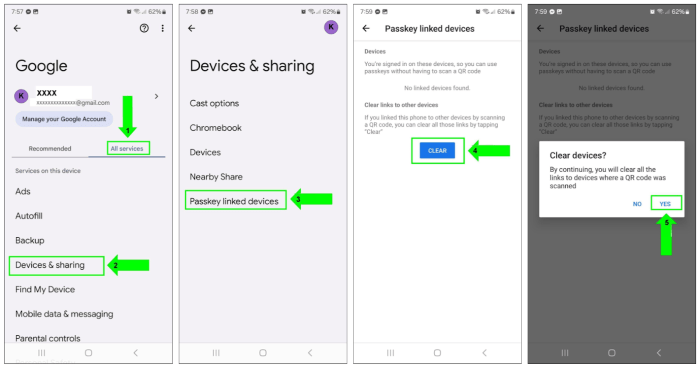
Strategies to Take away Undesirable Certificates
Eliminating these undesirable digital certificates in your Android is like decluttering your telephone – important for easy operation and safety. These certificates, whereas typically respectable, can pose dangers if they don’t seem to be correctly managed. This part particulars the really useful procedures for safely eradicating these digital artifacts out of your machine.Understanding how one can take away these certificates is essential. Eradicating them successfully ensures a cleaner, safer Android expertise.
The strategies differ relying on the extent of entry you might have and the character of the certificates itself.
Guide Certificates Removing
This technique is good for customers comfy navigating Android’s settings and managing safety particulars. It offers a excessive diploma of management and lets you selectively take away certificates.
This technique requires a user-friendly strategy, specializing in readability and ease. The steps are detailed to permit for straightforward comprehension and execution by Android customers.
- Find the certificates administration part. This typically entails navigating by means of the machine’s settings, sometimes discovered below safety or app administration. The precise location can differ barely primarily based on the Android model.
- Determine the undesirable certificates. Fastidiously overview the record of put in certificates to pinpoint the one you want to take away. Take note of the certificates’s topic (e.g., the web site or entity it is related to). In case you are uncertain, it’s best to seek the advice of a trusted supply or skilled for help.
- Provoke the removing course of. Comply with the on-screen prompts to verify the removing. This typically entails choosing the certificates and confirming the motion. Be conscious of any warnings or prompts displayed, as these may point out the significance of the certificates or potential penalties of removing.
- Confirm the removing. After affirmation, test that the certificates is now not current within the record of put in certificates. This step ensures that the removing was profitable and avoids potential future points.
Automated Certificates Removing
Some Android gadgets may help automated certificates administration instruments. This strategy simplifies the method for customers unfamiliar with guide strategies.
Utilizing automation instruments is commonly sooner and simpler than guide strategies, nevertheless it requires familiarity with the instrument’s interface and particular settings. It is essential to fastidiously overview the instrument’s functionalities earlier than utilizing it. Some instruments could provide granular management, permitting customers to selectively take away particular certificates, whereas others could require removing of whole certificates teams.
- Use devoted safety functions. Some apps focus on managing digital certificates and supply automated removing choices. Analysis and set up such apps from respected sources to keep away from potential safety dangers. These functions are significantly helpful for customers who should not comfy with guide removing strategies or who regularly must handle certificates.
- Discover system-level choices. Some Android variations or producers could present automated certificates removing capabilities throughout the machine’s safety settings. Discuss with your machine’s documentation for particular directions and tips.
Instance Situation: Eradicating a Malicious Certificates
Think about you think a lately put in app has added a malicious certificates to your machine. Guide removing would contain figuring out the certificates related to that app, then following the steps detailed above. It is a severe safety subject, and performing rapidly is essential. Automated instruments can be utilized, too, however thorough analysis and verification of the removing are essential.
Prevention Methods for Undesirable Certificates
Defending your Android machine from malicious certificates is paramount. These digital signatures, performing as passports for web sites and apps, will be exploited if not fastidiously managed. By understanding and implementing preventative measures, you considerably scale back the danger of falling sufferer to fraudulent actions. Implementing proactive measures is vital to safeguarding your machine’s integrity and your private info.Realizing how one can determine and keep away from probably dangerous certificates is a vital first step.
It is akin to studying to identify a suspicious character in a crowd—you develop an intuition for hazard. This proactive strategy lets you keep management over your machine’s safety posture, safeguarding towards malicious actors.
Configuring Android Safety Settings
Correctly configuring Android’s safety settings is important to stop undesirable certificates installations. The machine’s safety framework offers layers of safety towards unauthorized certificates additions. Cautious configuration of those settings kinds a sturdy barrier towards potential threats.
- Allow Certificates Verification: Actively checking the authenticity of certificates is a basic safety observe. Guarantee your machine is configured to confirm the validity of digital signatures earlier than trusting them. This important step prevents the set up of self-signed or compromised certificates, which might result in safety breaches.
- Prohibit Set up Sources: Restrict the sources from which your machine can set up certificates. This can stop probably malicious apps from putting in certificates with out your specific permission. By controlling set up sources, you restrict the avenues for malicious actors to introduce compromised certificates.
- Overview Certificates Permissions: Earlier than granting permission for certificates set up, fastidiously scrutinize the permissions requested. This strategy helps keep away from unknowingly granting entry to probably dangerous functions. Completely overview the requested permissions earlier than granting them, as this prevents unknowingly enabling dangerous apps.
Safety Practices to Keep away from Malicious Installations
Implementing sound safety practices is important for stopping undesirable certificates installations. These practices are like constructing a robust fortress round your digital belongings. A multi-layered strategy ensures a complete defence towards malicious actors.
- Replace Your Android System Frequently: Conserving your Android working system up to date is a proactive safety measure. Common updates typically embody safety patches that handle vulnerabilities, defending your machine from certificate-related exploits. By staying up to date, you leverage the most recent safety enhancements.
- Use a Respected VPN: Utilizing a digital personal community (VPN) can encrypt your web visitors and defend your machine from potential assaults. This encryption course of acts as a protecting protect, stopping interception and manipulation of your machine’s certificates interactions. Think about using a VPN to bolster your safety posture.
- Be Cautious of Public Wi-Fi Networks: Keep away from putting in certificates on public Wi-Fi networks. These networks are sometimes unsecured and inclined to assaults. Connecting to public Wi-Fi with out sufficient safety precautions can expose your machine to certificate-related vulnerabilities.
Greatest Practices for Certificates Administration and Verification
Efficient certificates administration and verification are essential to stop undesirable certificates. These practices are like having a talented safety guard watching over your digital belongings. Implementing them helps be sure that your certificates are respectable and reliable.
- Make use of Sturdy Passwords: Use robust and distinctive passwords on your machine and accounts. Sturdy passwords make it tougher for malicious actors to achieve entry to your certificates. This preventative measure enhances your machine’s safety posture.
- Belief Solely Verified Sources: Belief solely certificates from verified sources. Keep away from putting in certificates from untrusted or unknown sources. By adhering to this precept, you reduce the danger of putting in malicious certificates.
- Scrutinize Certificates Particulars: Fastidiously look at certificates particulars earlier than set up. This contains checking the issuer, validity interval, and different related info. This diligence helps stop set up of compromised or fraudulent certificates.
Prevention Technique Abstract
| Prevention Technique | Description | Implementation |
|---|---|---|
| Allow Certificates Verification | Confirm certificates authenticity | Configure machine settings |
| Prohibit Set up Sources | Restrict certificates set up sources | Configure app permissions |
| Overview Certificates Permissions | Scrutinize permissions earlier than granting | Completely look at requested permissions |
| Replace Android System Frequently | Apply safety patches | Guarantee common OS updates |
| Use a Respected VPN | Encrypt web visitors | Choose a reliable VPN supplier |
| Be Cautious of Public Wi-Fi | Keep away from putting in certificates on public Wi-Fi | Use safe connections each time doable |
| Make use of Sturdy Passwords | Improve account safety | Use robust and distinctive passwords |
| Belief Solely Verified Sources | Set up certificates from trusted sources | Confirm certificates issuers |
| Scrutinize Certificates Particulars | Examine certificates validity and issuer | Study certificates attributes fastidiously |
Illustrative Examples of Malicious Certificates: What Safety Certificates Ought to Not Be On My Android
Think about a digital unhealthy man, armed with a cast certificates, making an attempt to trick your Android machine into trusting a faux web site. This seemingly innocent doc, a digital passport, may very well be the important thing to unlocking delicate information or putting in dangerous software program. Understanding how these malicious certificates function is essential to safeguarding your machine.
A Fictitious Malicious Certificates
This malicious certificates, disguised as a respectable banking website, is designed to seize consumer credentials. It purports to be issued by a trusted authority however, in actuality, is a counterfeit. This deception is facilitated by a cleverly crafted digital signature that mimics the respectable authority’s signature.
Compromising a Gadget with a Malicious Certificates
The solid certificates, offered throughout a seemingly respectable on-line transaction, can mislead the machine into establishing a safe reference to a fraudulent server. The machine, believing it is interacting with a trusted entity, proceeds to transmit delicate information, like usernames and passwords. This information then falls into the fingers of the malicious actor behind the fraudulent website.
Creation and Distribution of Malicious Certificates
Making a malicious certificates requires technical experience. Malicious actors may exploit vulnerabilities in certificates authorities or use compromised techniques to generate and signal fraudulent certificates. Distribution can happen by means of numerous means, similar to malicious apps, compromised web sites, and even phishing emails. Usually, they leverage subtle strategies to make the certificates look genuine, hiding the malicious intent.
Exploitation Situation
Think about a consumer logging into their on-line banking account by means of a seemingly respectable cellular banking app. The app makes use of a malicious certificates to ascertain a reference to a fraudulent server. The consumer, unaware of the deception, enters their login credentials, that are instantly intercepted by the attacker. This might result in unauthorized entry to their financial institution accounts and monetary losses.
Instance Malicious Certificates
Certificates: -----BEGIN CERTIFICATE----- MIIDIzCCAf2gAwIBAgIJANi284p0d23MA0GCSqGSIb3DQEBBQUAMIGJMQswCQYD VQQGEwJHQjEQMA4GA1UEChMHU2VydmljZWxSZW1hc2gxDzANBgNVBAMMB2RvbWUg a2V5MB4XDTA5MDExMjE1MDU1NFoXDTA5MDExMjE2MDU1NFowgYkxCzAJBgNVBAYT AkpCMRAwDgYDVQQKEwdTZXJ2aWNlUm1hc2gxDzANBgNVBAMMB2RvbWUgS2V5MRww GgYJKoZIhvcNAQkBFhN0ZXJ2aWNlQGV4YW1wbGUuY29tMQswCQYDVQQGEwJHQjEQ MA4GA1UEChMHU2VydmljZWxSZW1hc2gxDzANBgNVBAMMB2RvbWUgS2V5MIIBIjANBgk qhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAnp1c4X7X8aQ25pK8Z7+4+8m1691263 7v46b13m50t8k07qZ2d5/955uZ7i3xW/1i5m0u8q258e/Z5v60X8zG8X5zK46m1s7e Xq5h95+t08371m+w92a5xQ45q5+dQ+7f2mQ3Q6Yv/qZ18+m3/h/9c8t4k8b40Y+tX 2t21Z61x0435gJ7+24m+b6X79860+m5n6y+v9l49m1qN35i5f75k3r/qP3e3z50e kQ4v5+c02h6jW1hG+j1gS+eY/c1241b+19eH0/u6aV/b0dQIDAQABo4IC5jANBgkqhki G9w0BAQSBggrBgEFBQcwAoYICAQQDMB0GCSqGSIb3DQEBCwUAMIGIMQswCQYDVQQG EwJHQjEQMA4GA1UEChMHU2VydmljZWxSZW1hc2gxDzANBgNVBAMMB2RvbWUgS2V5 MBgGCSqGSIb3DQEBCwUAMH0GCSqGSIb3DQEBAQUAA4IBDwAwggEWAgEAMIIBCgKCAQ EAq4t3v7p99h0a83y12b669n5+2h/yY2bY9Y708l5a2j798q50h8o55s19k0h3Z9x +708b7a143w/5y809o74g21929v832jX9a0f810q+a6e5u4f1eJ850853v/908wY v220w8aZ9t+q7c776313zQ92e8t1m60jZ0vW7n1x1hG8r8p6+2a0693b2Y4283X97 mZ6s+3h7o/t5m9X7tX+o+k4vQ95a4d1z9Z/9d2s8z59s79e62x94vZ4y04eG16l4q CAwEAAaNMEswCQYDVQQGEwJHQjEQMA4GA1UEChMHU2VydmljZWxSZW1hc2gxDzAN BgNVBAMMB2RvbWUgS2V5MB4XDTA5MDExMjE1MDU1NFowgYkxCzAJBgNVBAYTAkp CMRAwDgYDVQQKEwdTZXJ2aWNlUm1hc2gxDzANBgNVBAMMB2RvbWUgS2V5MIIBIjAN BgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAq4t3v7p99h0a83y12b669n5+2h/y Y2bY9Y708l5a2j798q50h8o55s19k0h3Z9x+708b7a143w/5y809o74g21929v832 jX9a0f810q+a6e5u4f1eJ850853v/908wYv220w8aZ9t+q7c776313zQ92e8t1m60 jZ0vW7n1x1hG8r8p6+2a0693b2Y4283X97mZ6s+3h7o/t5m9X7tX+o+k4vQ95a4d1 z9Z/9d2s8z59s79e62x94vZ4y04eG16l4q -----END CERTIFICATE-----
This instance is for illustrative functions solely and shouldn’t be used for precise verification. Discover the possibly malicious topic, issuer, and different particulars.
Superior Issues for Certificates Administration
Navigating the intricate world of digital certificates requires a deeper understanding past primary identification and removing. This part delves into the delicate features of certificates administration on Android, inspecting the essential roles of authorities, belief shops, and revocation mechanisms. Understanding these superior ideas is important for sustaining a sturdy and safe Android ecosystem.
Superior certificates administration entails a multifaceted strategy, incorporating a layered system of checks and balances to make sure trustworthiness. Android’s safety structure leverages the intricate interaction of certificates authorities, belief shops, and revocation lists to validate certificates and defend towards malicious actors. This intricate system ensures solely trusted entities can subject and make the most of digital certificates.
Certificates Authorities and Belief Shops
Android depends on trusted Certificates Authorities (CAs) to subject and validate digital certificates. These CAs are entities with a confirmed observe document of reliability, vetted and acknowledged for his or her safety practices. Android’s belief retailer is a pre-loaded record of trusted CAs, making certain the working system solely trusts certificates from acknowledged authorities. This prevents malicious actors from circumventing safety measures by creating fraudulent certificates that masquerade as respectable ones.
Certificates Revocation Lists, What safety certificates shouldn’t be on my android
Certificates revocation lists (CRLs) play a crucial function within the certificates validation course of. These lists comprise a document of certificates which have been revoked as a consequence of compromise or different safety considerations. Android gadgets routinely test these lists to make sure certificates are nonetheless legitimate and trusted. This proactive strategy helps to determine and mitigate the danger of utilizing compromised certificates, enhancing total safety posture.
Think about a system of public notices, flagging compromised certificates for fast motion.
Certificates Administration inside Apps and Providers
Managing certificates inside particular apps and providers requires cautious consideration of the safety implications. Totally different apps might have to make use of particular certificates for safe communication, probably for accessing delicate information or providers. Safe storage and administration of those certificates throughout the software are essential, requiring meticulous dealing with to keep away from vulnerabilities. This meticulous strategy safeguards delicate information exchanged between apps and providers.
The Certificates Validation Course of (Flowchart)
The certificates validation course of is a crucial sequence of steps, from preliminary request to ultimate verification. A flowchart depicting this course of would showcase the next phases:
- Request Initiation: A shopper software initiates a safe connection request, which triggers the validation course of.
- Certificates Retrieval: The server offers the certificates to the shopper.
- Belief Retailer Verification: The Android machine consults its pre-loaded belief retailer to test the validity of the CA issuing the certificates.
- CRL Examine: The machine verifies the certificates towards the suitable CRL to make sure it hasn’t been revoked.
- Certificates Validation: The certificates’s validity and authenticity are completely examined, verifying all the chain of belief.
- Connection Established: If all checks cross, the connection is established; in any other case, the connection is refused.
This detailed flowchart illustrates the systematic strategy Android employs to confirm certificates, bolstering its safety posture.
